Secure Multi Git Remote
Rohan Büchner / March 28, 2022
READING TIME • ––– views
In this post, I'll explain how to set up a local dev environment that supports multiple upstream git branches, with unique ssh keys with a twist.
Most (non-self-employed) engineers these days will have their own Github (or another git provider) account, and at least one other... normally for their employer.
I've been using the below setup for a while, and recently decided to do a small upgrade to the way I do my local ssh... so I decided to blog about it.
In the example below, I'll use Developer `Bob` who works for the `Acme Company`.
1: Create a global `.gitconfig`
[user]
name = bob-forapples
email = bob-forapples@google.com
# employer specific git configs
[includeIf "gitdir:Sources/acme/"]
path = /Users/bob/Sources/acme/.gitconfig2: Create a local `.gitconfig`
... at the path `/Users/bob/Sources/acme/.gitconfig`. create as many of these as you need
[user]
name = bob-acme
email = bob@acme.comThe steps above will ensure when Bob commits in repos inside the acme folder, they will use his ace name & email.
3: Create or update the `.ssh/config`
... with the following
# Personal account
Host github.com
HostName github.com
User git
IdentityFile ~/.ssh/id
# Work account, create as many as these as you need
Host acme.github.com
HostName github.com
User git
IdentityFile ~/.ssh/id_acme4: Clone a repo
The only trick now is to remember Bob's convention that you set up. If Bob clone's a repo from Acme,
he needs to slightly alter the git clone command to match the host of where he's using what specific ssh key...
git clone git@acme.github.com:git/repo_name.git5: Bonus Secure your SSH keys.
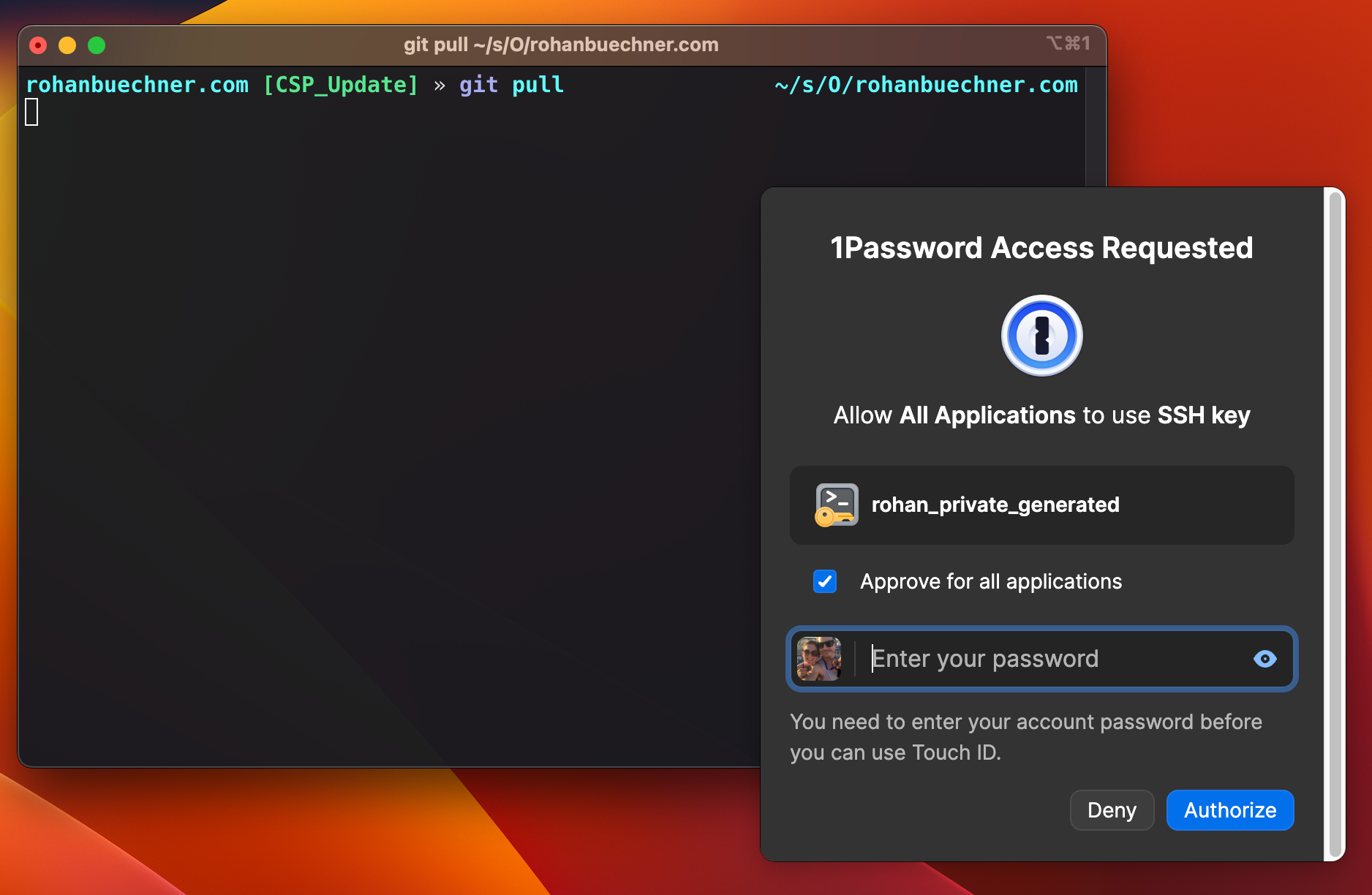
As of 1Password 8. You can now store your SSH keys inside a vault. I prefer this to have a potential mess of files that I no longer remember where they are or aren't being used.
Another major benefit is that during the regular workflow of using said ssh keys your CLI 1Password will just pop up a little biometric login prompt, you scan your fingerprint, and you're authorized to use your key in that session. So simple, and so damn cool.
To achieve all of the above you need to do the following.
- Upgrade to 1Password8 (if you're on an older version)
- In 1Password, got to Preferences > Developer
- Enable Use SSH Agent
- Enable Biometric unlock for CLI
- Add your key to the vault and export the pub key.
- Store the pub key in your `.ssh` folder
Next, create a symlink for the agent:
mkdir -p ~/.1password && ln -s ~/Library/Group\ Containers/2BUA8C4S2C.com.1password/t/agent.sock ~/.1password/agent.sockand update your `.ssh/config`
Host *
IdentitiesOnly yes
# this tells gh to use the 1Password Identity agent for all hosts
IdentityAgent "~/.1password/agent.sock"
Host github.com
HostName github.com
User git
IdentityFile ~/.ssh/id.pub
Host acme.github.com
HostName github.com
User git
IdentityFile ~/.ssh/id_acme.pub